A hash function is a cryptographic algorithm which is used to transform large random size data to small fixed size data. The data output of the hash algorithm is called hash value or digest. The basic operation of hash functions does not need any key and operate in a one-way manner.a push button on a telephone or key on a computer keyboard that is marked with a hash mark (#); pound key ( def ). Computers. hash value.A hash table is a data structure that is used to store keys/value pairs. It uses a hash function to compute an index into an array in which an element will be inserted or searched. By using a good hash function, hashing can work well.
Do you need a key for SHA-256 : No, SHA256 does not require a key.
Does SHA require a key
all SHA-1 hash value will have 160 bits. That is whether you give single character or 100000 character, the output size will be 160 bits only. So SHA-1 don't need key. It is used for Authentication purpose.
Is hash a private key : With a digital signature, a private key is used to create a hash value of the contents of the file that's being signed and sent. The recipient uses the signer's public key to decrypt the signature and verify that the decrypted hash value matches the hash of the original file.
How do you make a hashtag sign on a keyboard To create the hash symbol using a U.S. keyboard on a Windows, macOS, or Linux computer, hold down Shift and press the number 3 at the top of the keyboard. Doing the Alt code Alt +35 can also create a hash. Hashtable stores key/value pair in hash table. In Hashtable we specify an object that is used as a key, and the value we want to associate to that key. The key is then hashed, and the resulting hash code is used as the index at which the value is stored within the table.
What is the search key in hashing
A hash function h=hash(e) uses the key value key(e) to determine the bin A[h] into which to insert e, where 0≤h<b. Once the hash table A is constructed, then searching for an item t is transformed into a search for t within A[h] where h=hash(t).Consequently, before a cipher can work, both the sender and receiver must have a key or a set of keys. Cryptographic ciphers are used to convert ciphertext to plaintext and back. With symmetric key algorithms, the same key is used for the encryption and decryption of data.all SHA-1 hash value will have 160 bits. That is whether you give single character or 100000 character, the output size will be 160 bits only. So SHA-1 don't need key. SHA1 doesn't have a concept of keys at all. It's just a hash function.
Is hash public key : Hash functions are a fundamental component of digital signatures. In digital signature schemes, a hash of the message is signed by a private key. Recipients can verify the signature using the sender's public key and comparing the computed hash with the received hash value.
Can hash be a primary key : Using a Hash or GUID as Primary Key is also bad idea because it causes Index Fragmentation and frequent Page Splits.
How to add key to hash
In Ruby, a new key-value pair can be added to a hash using bracket notation. The new key is bracketed after the name of the hash and then the value is assigned after the equals sign. Hash#has_key() is a Hash class method which checks whether the given key is present in hash.
Syntax: Hash.has_key()
Parameter: Hash values.
Return: true – if the key is present otherwise return false.
Hash keys specify the criteria used to determine the partition into which the hash partitioner assigns a record. The hash partitioner guarantees to assign all records with identical hash keys to the same partition. The hash partitioner lets you set a primary key and multiple secondary keys.
What is a keyed hash function : Definitions: An algorithm that creates a message authentication code based on both a message and a secret key shared by two endpoints. Also known as a hash message authentication code algorithm.
Antwort Does hash need a key? Weitere Antworten – Does hashing need a key
A hash function is a cryptographic algorithm which is used to transform large random size data to small fixed size data. The data output of the hash algorithm is called hash value or digest. The basic operation of hash functions does not need any key and operate in a one-way manner.a push button on a telephone or key on a computer keyboard that is marked with a hash mark (#); pound key ( def ). Computers. hash value.A hash table is a data structure that is used to store keys/value pairs. It uses a hash function to compute an index into an array in which an element will be inserted or searched. By using a good hash function, hashing can work well.
Do you need a key for SHA-256 : No, SHA256 does not require a key.
Does SHA require a key
all SHA-1 hash value will have 160 bits. That is whether you give single character or 100000 character, the output size will be 160 bits only. So SHA-1 don't need key. It is used for Authentication purpose.
Is hash a private key : With a digital signature, a private key is used to create a hash value of the contents of the file that's being signed and sent. The recipient uses the signer's public key to decrypt the signature and verify that the decrypted hash value matches the hash of the original file.
How do you make a hashtag sign on a keyboard To create the hash symbol using a U.S. keyboard on a Windows, macOS, or Linux computer, hold down Shift and press the number 3 at the top of the keyboard. Doing the Alt code Alt +35 can also create a hash.
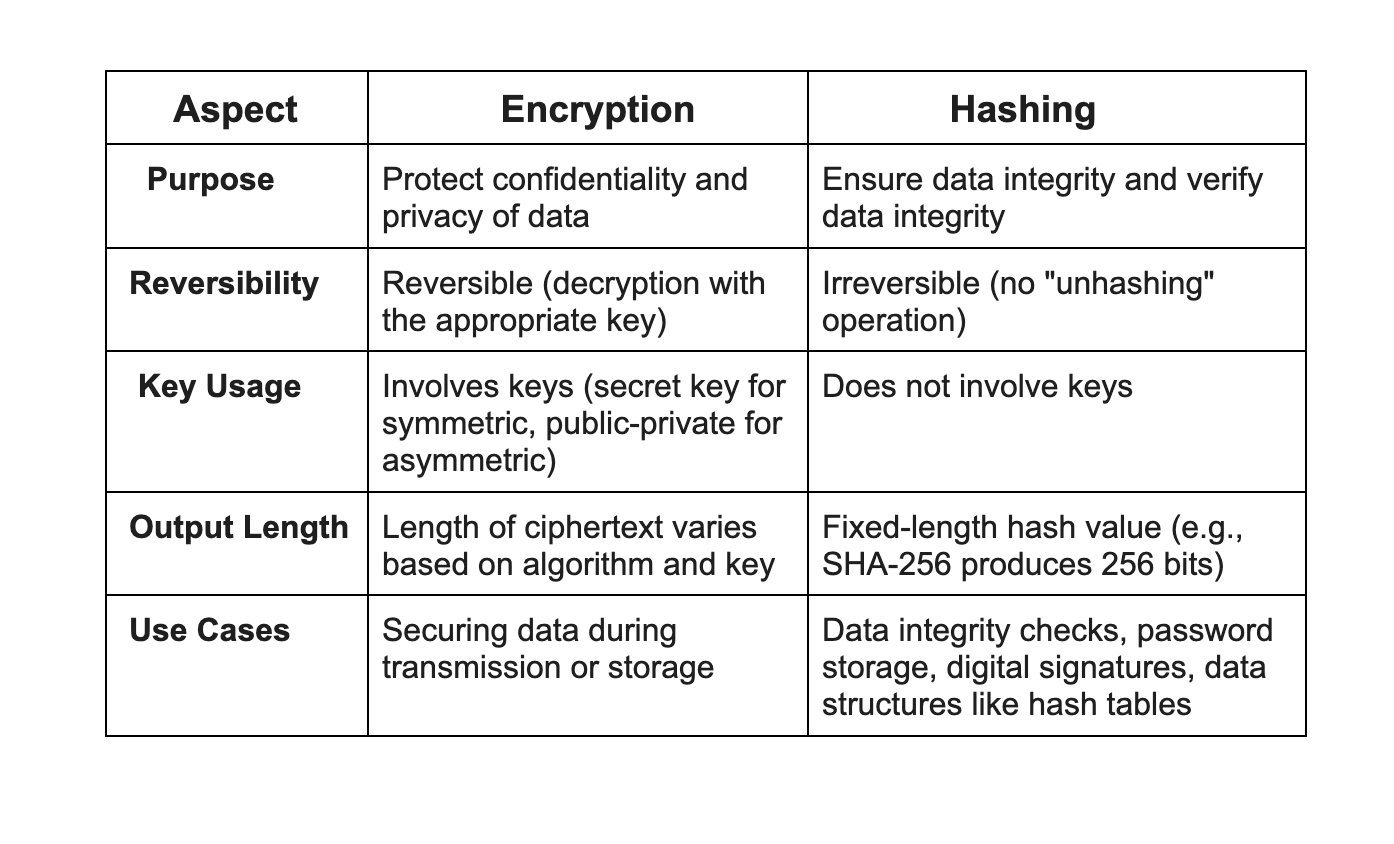
Hashtable stores key/value pair in hash table. In Hashtable we specify an object that is used as a key, and the value we want to associate to that key. The key is then hashed, and the resulting hash code is used as the index at which the value is stored within the table.
What is the search key in hashing
A hash function h=hash(e) uses the key value key(e) to determine the bin A[h] into which to insert e, where 0≤h<b. Once the hash table A is constructed, then searching for an item t is transformed into a search for t within A[h] where h=hash(t).Consequently, before a cipher can work, both the sender and receiver must have a key or a set of keys. Cryptographic ciphers are used to convert ciphertext to plaintext and back. With symmetric key algorithms, the same key is used for the encryption and decryption of data.all SHA-1 hash value will have 160 bits. That is whether you give single character or 100000 character, the output size will be 160 bits only. So SHA-1 don't need key.

SHA1 doesn't have a concept of keys at all. It's just a hash function.
Is hash public key : Hash functions are a fundamental component of digital signatures. In digital signature schemes, a hash of the message is signed by a private key. Recipients can verify the signature using the sender's public key and comparing the computed hash with the received hash value.
Can hash be a primary key : Using a Hash or GUID as Primary Key is also bad idea because it causes Index Fragmentation and frequent Page Splits.
How to add key to hash
In Ruby, a new key-value pair can be added to a hash using bracket notation. The new key is bracketed after the name of the hash and then the value is assigned after the equals sign.
Hash#has_key() is a Hash class method which checks whether the given key is present in hash.
Hash keys specify the criteria used to determine the partition into which the hash partitioner assigns a record. The hash partitioner guarantees to assign all records with identical hash keys to the same partition. The hash partitioner lets you set a primary key and multiple secondary keys.
What is a keyed hash function : Definitions: An algorithm that creates a message authentication code based on both a message and a secret key shared by two endpoints. Also known as a hash message authentication code algorithm.