Basically, encryption is the process of scrambling plaintext into unreadable ciphertext, which you can decrypt with a relevant key, while hashing turns plain text into a unique code, which can't be reverted into a readable form.Instead, we use a process called hashing to obscure the plaintext password in storage, in a way that ensures we can still verify your password when you log in using plaintext. Hashing is a one-way encryption of the password — with one-way simply meaning that once encrypted the data cannot be decrypted.No, hashed data cannot be decrypted. Hashing is a one-way process, which means that the original data cannot be obtained from the hash value. It is designed to be irreversible, making it suitable for storing passwords and verifying data integrity.
What does hash mean in cyber security : Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.
Is MD5 hash or encryption
MD5 (Message Digest Method 5) is a cryptographic hash algorithm used to generate a 128-bit digest from a string of any length. It represents the digests as 32 digit hexadecimal numbers. Ronald Rivest designed this algorithm in 1991 to provide the means for digital signature verification.
Is hash a type of cryptography : A cryptographic hash function is a mathematical function used in cryptography. Typical hash functions take inputs of variable lengths to return outputs of a fixed length. A cryptographic hash function combines the message-passing capabilities of hash functions with security properties.
Hashes can also be insecure due to rainbow tables or hash collisions. We should be aware of what hash algorithms are good to use and which ones are no longer perceived as secure. Insecure hash isn't an attack but is a symptom of a larger attack. Many legacy systems still use MD5 as a hash function to store passwords. Dictionary attack.
Attackers will use software to run popular and predictable passwords through commonly used hashing algorithms. The program will compare the hashed results with the scrambled credentials in the hacker's possession. If there's a match, the hacker can easily deduce the original password.
Is hashed data readable
Hashing is a method of turning readable data into unique but unreadable data — this can be applied to PII to protect the values in a way that they can still be used to link datasets.You can't unhash. Hashing is a one-way function.Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Although the terms “hashing” and “encryption” may be used interchangeably, hashing is always used for the purposes of one-way encryption, and hashed values are very difficult to decode.
Is MD5 hash still secure : Vulnerabilities: The MD5 algorithm has long been considered insecure for cryptographic purposes due to significant vulnerabilities. Researchers have demonstrated practical collision attacks against MD5, which allows for the creation of different inputs that produce the same hash value.
Is SHA256 safer than MD5 : SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.
Can hashed passwords be hacked
If they successfully crack a hashed password, they may gain unauthorized access to user accounts and steal sensitive information. They may also use the stolen information for ransomware attacks, where the organization has to pay large sums of money to regain the sensitive data hackers have stolen and encrypted. What is SHA-256 The SHA-256 algorithm is one flavor of SHA-2 (Secure Hash Algorithm 2), which was created by the National Security Agency in 2001 as a successor to SHA-1. SHA-256 is a patented cryptographic hash function that outputs a value that is 256 bits long.By making a guess at a password, the attacker can compare the output of his SHA-256 against the SHA-256 that he finds in the database. And because passwords are so short, testing many password guesses this way is easy for a computer.
Which hash is secure : Common attacks like brute force attacks can take years or even decades to crack the hash digest, so SHA-2 is considered the most secure hash algorithm.
Antwort Does hash mean encryption? Weitere Antworten – Is hashing the same as encryption
Basically, encryption is the process of scrambling plaintext into unreadable ciphertext, which you can decrypt with a relevant key, while hashing turns plain text into a unique code, which can't be reverted into a readable form.Instead, we use a process called hashing to obscure the plaintext password in storage, in a way that ensures we can still verify your password when you log in using plaintext. Hashing is a one-way encryption of the password — with one-way simply meaning that once encrypted the data cannot be decrypted.No, hashed data cannot be decrypted. Hashing is a one-way process, which means that the original data cannot be obtained from the hash value. It is designed to be irreversible, making it suitable for storing passwords and verifying data integrity.
What does hash mean in cyber security : Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.
Is MD5 hash or encryption
MD5 (Message Digest Method 5) is a cryptographic hash algorithm used to generate a 128-bit digest from a string of any length. It represents the digests as 32 digit hexadecimal numbers. Ronald Rivest designed this algorithm in 1991 to provide the means for digital signature verification.
Is hash a type of cryptography : A cryptographic hash function is a mathematical function used in cryptography. Typical hash functions take inputs of variable lengths to return outputs of a fixed length. A cryptographic hash function combines the message-passing capabilities of hash functions with security properties.
Hashes can also be insecure due to rainbow tables or hash collisions. We should be aware of what hash algorithms are good to use and which ones are no longer perceived as secure. Insecure hash isn't an attack but is a symptom of a larger attack. Many legacy systems still use MD5 as a hash function to store passwords.
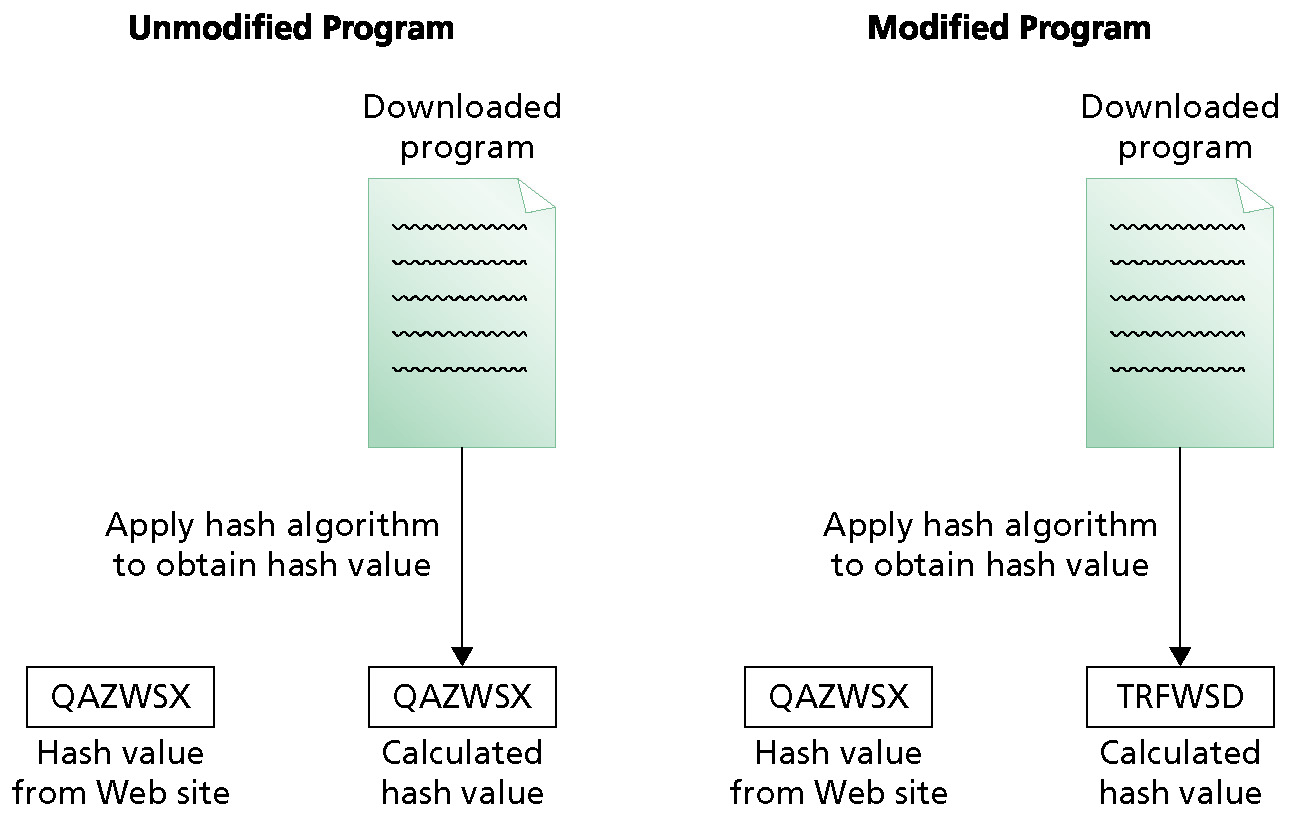
Dictionary attack.
Attackers will use software to run popular and predictable passwords through commonly used hashing algorithms. The program will compare the hashed results with the scrambled credentials in the hacker's possession. If there's a match, the hacker can easily deduce the original password.
Is hashed data readable
Hashing is a method of turning readable data into unique but unreadable data — this can be applied to PII to protect the values in a way that they can still be used to link datasets.You can't unhash. Hashing is a one-way function.Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string.
Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Although the terms “hashing” and “encryption” may be used interchangeably, hashing is always used for the purposes of one-way encryption, and hashed values are very difficult to decode.
Is MD5 hash still secure : Vulnerabilities: The MD5 algorithm has long been considered insecure for cryptographic purposes due to significant vulnerabilities. Researchers have demonstrated practical collision attacks against MD5, which allows for the creation of different inputs that produce the same hash value.
Is SHA256 safer than MD5 : SHA256 has several advantages over MD5 and SHA-1, such as producing a longer hash (256 bits) that is more resistant to collisions and brute-force attacks. Additionally, there are no known vulnerabilities or weaknesses with SHA256, unlike MD5 and SHA-1 which have been exploited by hackers and researchers.
Can hashed passwords be hacked
If they successfully crack a hashed password, they may gain unauthorized access to user accounts and steal sensitive information. They may also use the stolen information for ransomware attacks, where the organization has to pay large sums of money to regain the sensitive data hackers have stolen and encrypted.
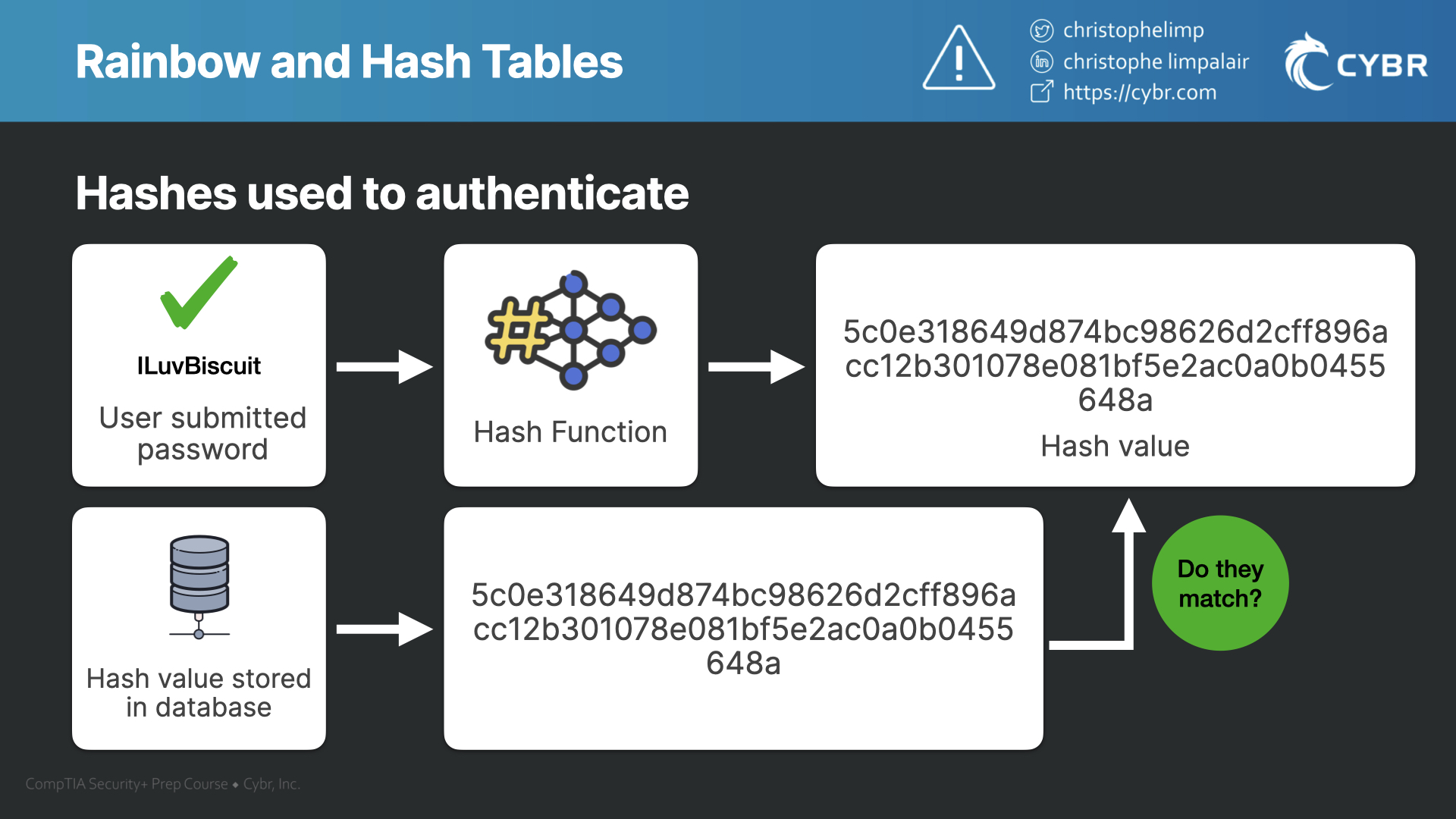
What is SHA-256 The SHA-256 algorithm is one flavor of SHA-2 (Secure Hash Algorithm 2), which was created by the National Security Agency in 2001 as a successor to SHA-1. SHA-256 is a patented cryptographic hash function that outputs a value that is 256 bits long.By making a guess at a password, the attacker can compare the output of his SHA-256 against the SHA-256 that he finds in the database. And because passwords are so short, testing many password guesses this way is easy for a computer.
Which hash is secure : Common attacks like brute force attacks can take years or even decades to crack the hash digest, so SHA-2 is considered the most secure hash algorithm.