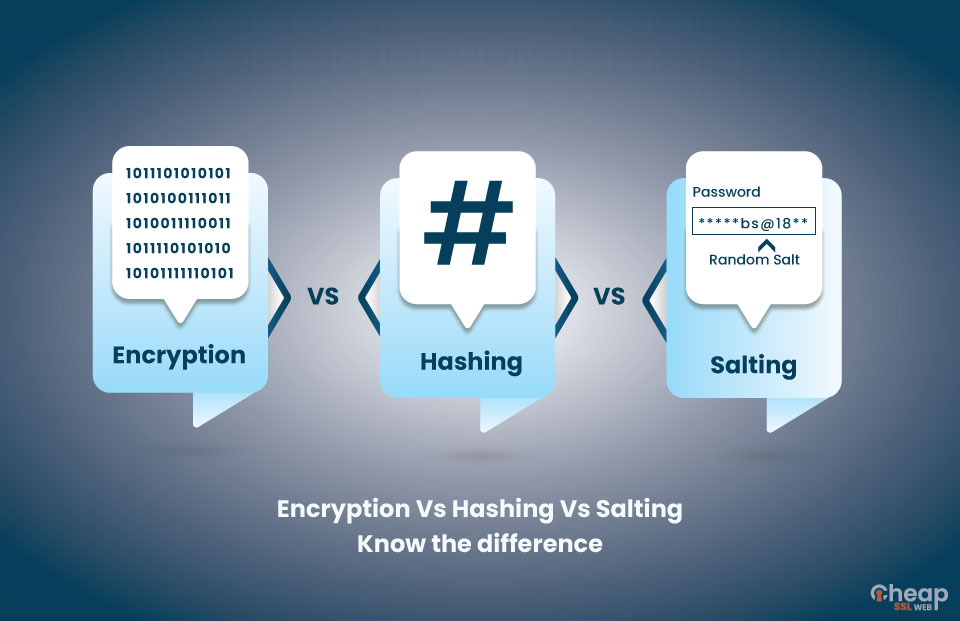
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.Data encryption is a method of converting data from a readable format (plaintext) into an unreadable, encoded format (ciphertext). Encrypted data can only be read or processed after it has been decrypted, using a decryption key or password.E2EE is "end-to-end" because it is impossible for anyone in the middle to decrypt the message. Users do not have to trust that the service they are using will not read their messages: it is not possible for the service to do so.
Is encryption reversible : Encryption is a reversible method of converting plaintext passwords to ciphertext, and you can return to the original plaintext with a decryption key. Encryption is often used for storing passwords in password managers.
Why is it impossible to unhash
Overall, the main reason why it is difficult or impossible to recover the original value from a given hash value is that the hash function is designed to be a one-way function, meaning that it is irreversible and computationally infeasible to reverse-engineer the original input data from the hash value.
Is it possible to Unhash SHA256 : SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted.
Additionally, I've written about how AI is creating new cyberattack vectors. Since it is widely understood that powerful quantum computers could break the internet's encryption and AI and machine learning (ML) are already causing global cyber issues, could AI/ML also be used for defense The short answer is, yes. Please note that VeraCrypt can in-place decrypt only partitions and drives (select System > Permanently Decrypt System Partition/Drive for system partition/drive and select Volumes -> Permanently Decrypt for non-system partition/drive).
Can end-to-end encryption be cracked
Vulnerability to Compromised Endpoints: End-to-end encryption relies on the endpoints' security — the devices used by the sender and recipient — to encrypt and decrypt the data. If either endpoint is compromised through malware, hacking, or physical access, it can undermine the effectiveness of end-to-end encryption.Conversation. Now as you can see this is the secret. Conversation just want to press and hold it and simply delete this conversation. So that is how you turn off end-to-end encryption in messenger.How does hashing work in crypto When used in Bitcoin and other cryptocurrencies, the end result is typically a 64-digit long string of numbers and letters. Because the conversion is done by a cryptographic algorithm (the “hash function”), the jumbling formula is unknown so the 64-digit string can't be reversed. Ideally, hash functions should be irreversible. Meaning that while it is quick and easy to compute the hash if you know the input message for any given hash function, it is very difficult to go through the process in reverse to compute the input message if you only know the hash value.
Can AI decrypt hash : No, you can't determine the first character of the plaintext from the hash, because there's no such thing as "the plaintext" for a given hash.
Is SHA-256 irreversible : Digest Length: The length of the hash digest should be 256 bits in SHA 256 algorithm, 512 bits in SHA-512, and so on. Bigger digests usually suggest significantly more calculations at the cost of speed and space. Irreversible: By design, all hash functions such as the SHA 256 are irreversible.
Is SHA-256 unbreakable
Bitcoin and other cryptocurrencies rely on SHA-256 to forge the unbreakable links between the blocks in a blockchain. In cryptography, the one-time pad (OTP) is an encryption technique that cannot be cracked, but requires the use of a single-use pre-shared key that is larger than or equal to the size of the message being sent. In this technique, a plaintext is paired with a random secret key (also referred to as a one-time pad).The most common method is stealing the encryption key itself. Another common way is intercepting the data either before it has been encrypted by the sender or after it has been decrypted by the recipient. Hackers deploy different approaches depending on whether the encryption is symmetric or asymmetric.
What is the weakness of VeraCrypt : Biggest flaw in VeraCrypt(or other Encryption programs) is Hash Algorithm. VeraCrypt hashes (SHA,Whirlpool,Streebog) it is the only point where can break an encrypted disk. Because break algorithm (AES,Towish,Camellia,Serpent,Kuznyechik) it is practically impossible.
Antwort Can we decrypt hashing? Weitere Antworten – Can you decrypt a hash
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.Data encryption is a method of converting data from a readable format (plaintext) into an unreadable, encoded format (ciphertext). Encrypted data can only be read or processed after it has been decrypted, using a decryption key or password.E2EE is "end-to-end" because it is impossible for anyone in the middle to decrypt the message. Users do not have to trust that the service they are using will not read their messages: it is not possible for the service to do so.
Is encryption reversible : Encryption is a reversible method of converting plaintext passwords to ciphertext, and you can return to the original plaintext with a decryption key. Encryption is often used for storing passwords in password managers.
Why is it impossible to unhash
Overall, the main reason why it is difficult or impossible to recover the original value from a given hash value is that the hash function is designed to be a one-way function, meaning that it is irreversible and computationally infeasible to reverse-engineer the original input data from the hash value.
Is it possible to Unhash SHA256 : SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted.
Additionally, I've written about how AI is creating new cyberattack vectors. Since it is widely understood that powerful quantum computers could break the internet's encryption and AI and machine learning (ML) are already causing global cyber issues, could AI/ML also be used for defense The short answer is, yes.
Please note that VeraCrypt can in-place decrypt only partitions and drives (select System > Permanently Decrypt System Partition/Drive for system partition/drive and select Volumes -> Permanently Decrypt for non-system partition/drive).
Can end-to-end encryption be cracked
Vulnerability to Compromised Endpoints: End-to-end encryption relies on the endpoints' security — the devices used by the sender and recipient — to encrypt and decrypt the data. If either endpoint is compromised through malware, hacking, or physical access, it can undermine the effectiveness of end-to-end encryption.Conversation. Now as you can see this is the secret. Conversation just want to press and hold it and simply delete this conversation. So that is how you turn off end-to-end encryption in messenger.How does hashing work in crypto When used in Bitcoin and other cryptocurrencies, the end result is typically a 64-digit long string of numbers and letters. Because the conversion is done by a cryptographic algorithm (the “hash function”), the jumbling formula is unknown so the 64-digit string can't be reversed.
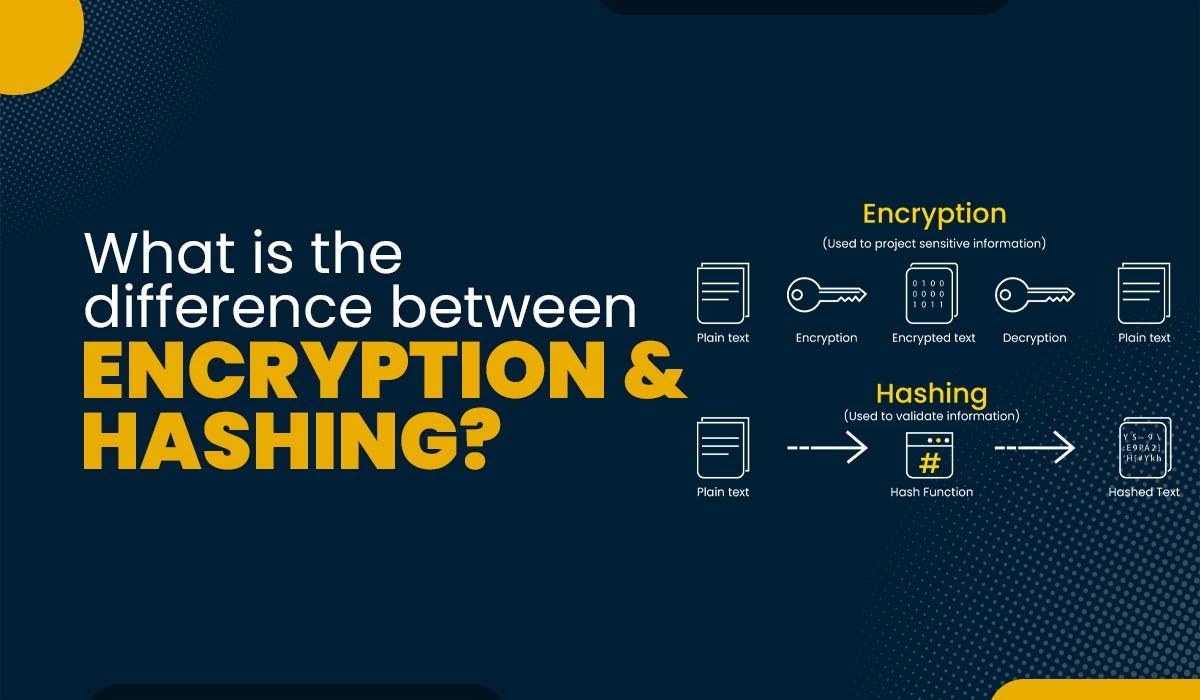
Ideally, hash functions should be irreversible. Meaning that while it is quick and easy to compute the hash if you know the input message for any given hash function, it is very difficult to go through the process in reverse to compute the input message if you only know the hash value.
Can AI decrypt hash : No, you can't determine the first character of the plaintext from the hash, because there's no such thing as "the plaintext" for a given hash.
Is SHA-256 irreversible : Digest Length: The length of the hash digest should be 256 bits in SHA 256 algorithm, 512 bits in SHA-512, and so on. Bigger digests usually suggest significantly more calculations at the cost of speed and space. Irreversible: By design, all hash functions such as the SHA 256 are irreversible.
Is SHA-256 unbreakable
Bitcoin and other cryptocurrencies rely on SHA-256 to forge the unbreakable links between the blocks in a blockchain.
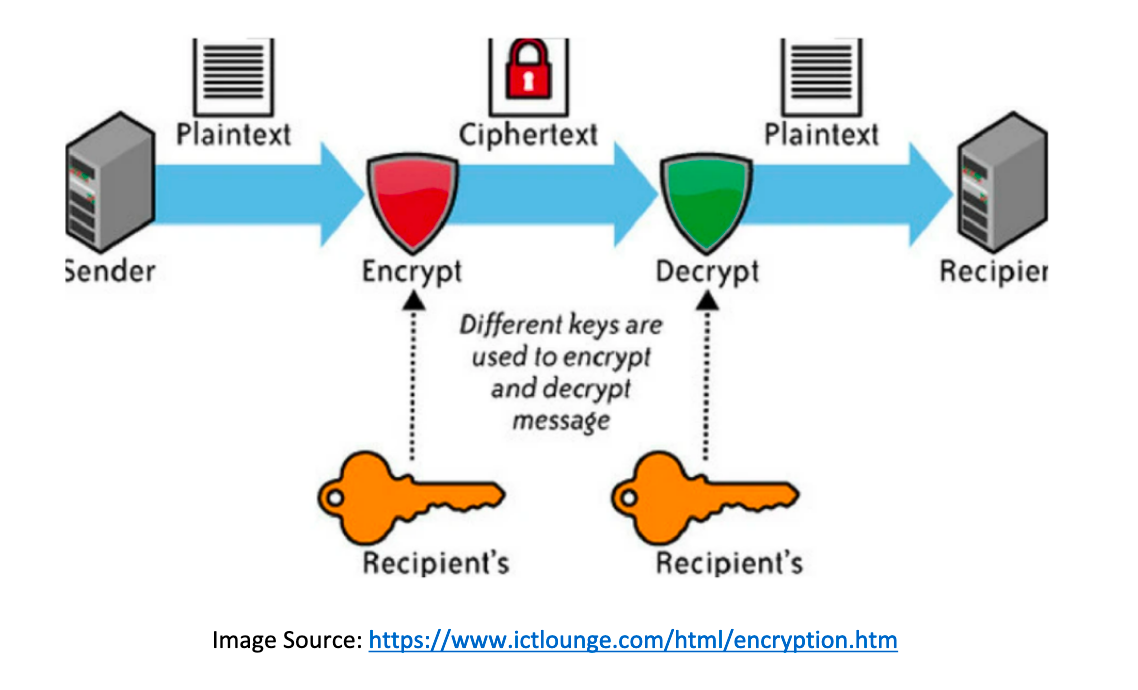
In cryptography, the one-time pad (OTP) is an encryption technique that cannot be cracked, but requires the use of a single-use pre-shared key that is larger than or equal to the size of the message being sent. In this technique, a plaintext is paired with a random secret key (also referred to as a one-time pad).The most common method is stealing the encryption key itself. Another common way is intercepting the data either before it has been encrypted by the sender or after it has been decrypted by the recipient. Hackers deploy different approaches depending on whether the encryption is symmetric or asymmetric.
What is the weakness of VeraCrypt : Biggest flaw in VeraCrypt(or other Encryption programs) is Hash Algorithm. VeraCrypt hashes (SHA,Whirlpool,Streebog) it is the only point where can break an encrypted disk. Because break algorithm (AES,Towish,Camellia,Serpent,Kuznyechik) it is practically impossible.