For example, a piece of plain text (a password, for example) can be turned into a hashed value, making it very hard to decipher. Hashing is a one-way process that can't be directly reversed (as opposed to encryption, which can be decrypted if you have the appropriate decryption key).One-way encryption is a type of encryption used to secure and protect passwords and other sensitive data. It encrypts the data by scrambling it and making it unreadable to anyone without special keys. One-way encryption is much tougher to crack compared to two-way encryption and can keep your data safe.Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Why is hashing irreversible : Hashing is generally a one-way function, which means that it is easy to convert a message into a hash but very difficult to “reverse hash” a hash value back to its original message as it requires a massive amount of computing power.
Are hashes one-way
Put simply, a hash function scrambles data to encrypt it, making it unreadable without special keys or difficult hacking techniques. While there are many types of two-way encryption, hash functions are one-way encryption, which makes them even tougher codes to crack.
Is sha256 one-way encryption : Overview
The SHA-256 algorithm generates an almost unique, fixed-size 256-bit (32-byte) hash. This is a one-way function, so the result cannot be decrypted back to the original value. Currently, SHA-2 hashing is widely used, as it is considered the most secure hashing algorithm in the cryptographic arena.
SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted. Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.
Can hashing be undone
The hash function is ONE-WAY only.
You can't take an existing hash and try to reverse it to find the input string. So if all you know is the hash, there's no way to know what the original input is. You can't “reverse engineer” or hack the hash.The data that is hashed cannot be practically "unhashed". Commonly used hashing algorithms include Message Digest (MDx) algorithms, such as MD5, and Secure Hash Algorithms (SHA), such as SHA-1 and the SHA-2 family that includes the widely used SHA-256 algorithm.Because the output of a hash function is a fixed-size sequence of characters, it is theoretically impossible to reverse-engineer the original input message from the hash value. This is known as the “one-way” property of hash functions. SHA-256 is a cryptographic (one-way) hash function, so there is no direct way to decode it. The entire purpose of a cryptographic hash function is that you can't undo it.
Why is SHA-256 irreversible : SHA-256 refers to the bit size of the hash output. In other words, the resulting hash value from SHA-256 is 256 bits long, which provides a significantly larger search space compared to its predecessor, making it computationally infeasible to reverse engineer the original input from the hash value.
Is it possible to decrypt a hash : Hashing is a one-way process that converts a password to ciphertext using hash algorithms. A hashed password cannot be decrypted, but a hacker can try to reverse engineer it.
Is SHA-256 easy to crack
Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken". Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.While the hash produced is irreversible, it's not pre-image resistant! Given the hash value of 0, I can very easily produce any number of inputs that produce that hash: 2, 4, 6, 8, 10, etc.
Can you decrypt a hash value : Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Antwort Can AI decrypt hash? Weitere Antworten – Is hashing better than encryption
For example, a piece of plain text (a password, for example) can be turned into a hashed value, making it very hard to decipher. Hashing is a one-way process that can't be directly reversed (as opposed to encryption, which can be decrypted if you have the appropriate decryption key).One-way encryption is a type of encryption used to secure and protect passwords and other sensitive data. It encrypts the data by scrambling it and making it unreadable to anyone without special keys. One-way encryption is much tougher to crack compared to two-way encryption and can keep your data safe.Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Why is hashing irreversible : Hashing is generally a one-way function, which means that it is easy to convert a message into a hash but very difficult to “reverse hash” a hash value back to its original message as it requires a massive amount of computing power.
Are hashes one-way
Put simply, a hash function scrambles data to encrypt it, making it unreadable without special keys or difficult hacking techniques. While there are many types of two-way encryption, hash functions are one-way encryption, which makes them even tougher codes to crack.
Is sha256 one-way encryption : Overview
The SHA-256 algorithm generates an almost unique, fixed-size 256-bit (32-byte) hash. This is a one-way function, so the result cannot be decrypted back to the original value. Currently, SHA-2 hashing is widely used, as it is considered the most secure hashing algorithm in the cryptographic arena.
SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted.

Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.
Can hashing be undone
The hash function is ONE-WAY only.
You can't take an existing hash and try to reverse it to find the input string. So if all you know is the hash, there's no way to know what the original input is. You can't “reverse engineer” or hack the hash.The data that is hashed cannot be practically "unhashed". Commonly used hashing algorithms include Message Digest (MDx) algorithms, such as MD5, and Secure Hash Algorithms (SHA), such as SHA-1 and the SHA-2 family that includes the widely used SHA-256 algorithm.Because the output of a hash function is a fixed-size sequence of characters, it is theoretically impossible to reverse-engineer the original input message from the hash value. This is known as the “one-way” property of hash functions.
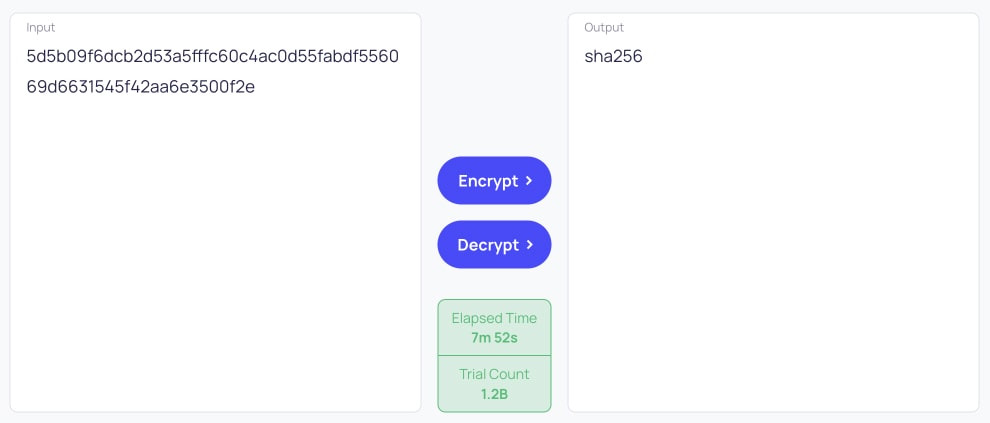
SHA-256 is a cryptographic (one-way) hash function, so there is no direct way to decode it. The entire purpose of a cryptographic hash function is that you can't undo it.
Why is SHA-256 irreversible : SHA-256 refers to the bit size of the hash output. In other words, the resulting hash value from SHA-256 is 256 bits long, which provides a significantly larger search space compared to its predecessor, making it computationally infeasible to reverse engineer the original input from the hash value.
Is it possible to decrypt a hash : Hashing is a one-way process that converts a password to ciphertext using hash algorithms. A hashed password cannot be decrypted, but a hacker can try to reverse engineer it.
Is SHA-256 easy to crack
Is it possible to crack the hashes produced by the SHA-256 algorithm without using a brute force attack No. If you could, then SHA-256 would be considered "broken".
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.While the hash produced is irreversible, it's not pre-image resistant! Given the hash value of 0, I can very easily produce any number of inputs that produce that hash: 2, 4, 6, 8, 10, etc.
Can you decrypt a hash value : Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.