To create a hash for a string value, follow these steps:
Open Visual Studio .
Create a new Console Application in Visual C# .
Use the using directive on the System , System.
Declare a string variable to hold your source data, and two byte arrays (of undefined size) to hold the source bytes and the resulting hash value.
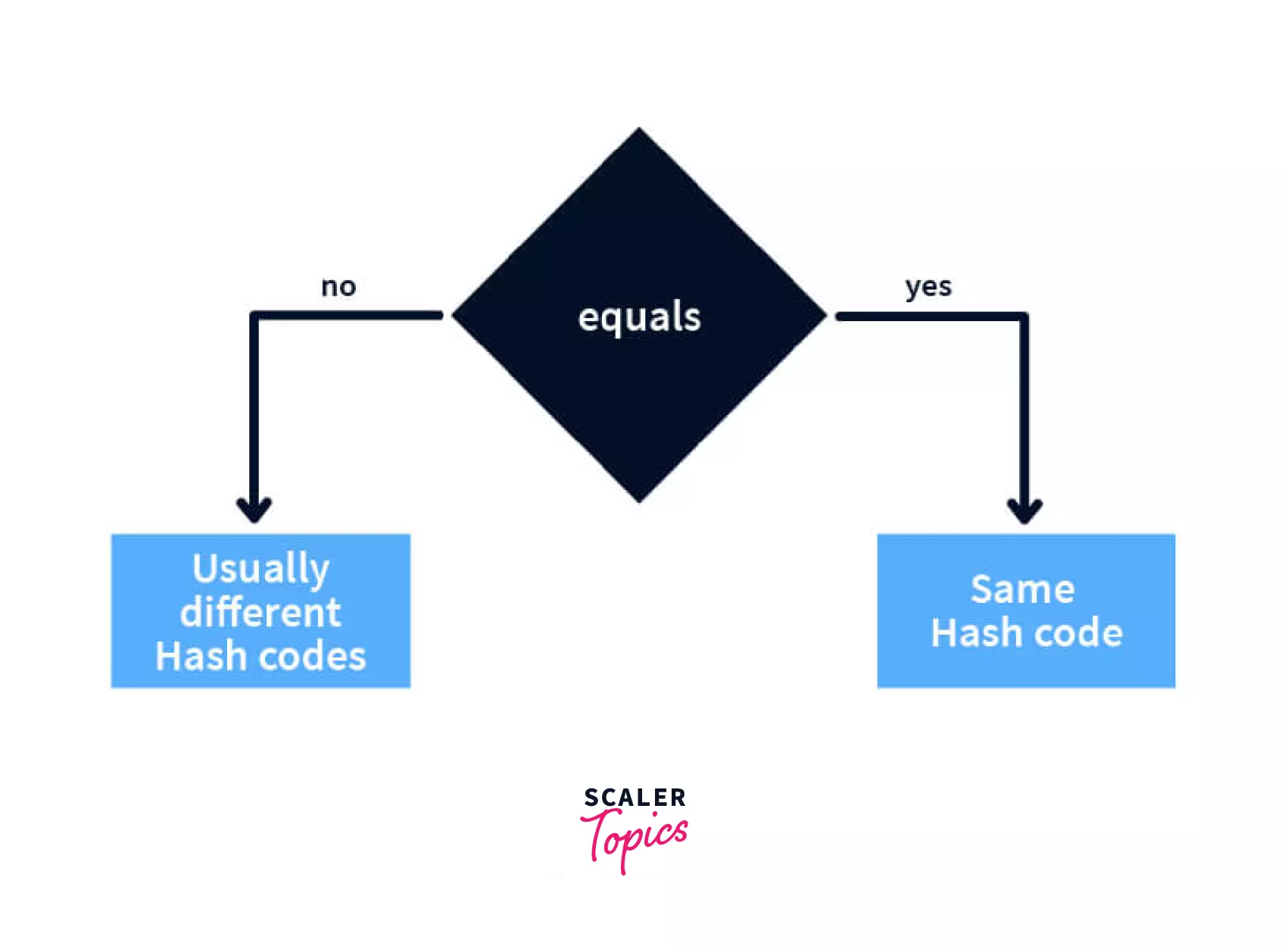
A hash code is a numeric value which is used to insert and identify an object in a hash-based collection. The GetHashCode method provides this hash code for algorithms that need quick checks of object equality.A hash value is a numeric value of a fixed length that uniquely identifies data. Hash values represent large amounts of data as much smaller numeric values, so they are used with digital signatures. You can sign a hash value more efficiently than signing the larger value.
How to verify hash values : You can use Windows Powershell to calculate the SHA-256 checksum for a file.
Open Windows Powershell.
Type Get-FileHash followed by a space.
Drag the downloaded ZIP file onto the Windows Powershell window after the Get-FileHash command.
Press Enter.
Compare the calculated hash value with the original hash value.
What is hash code number
A hash code is an integer value that is associated with each object in Java. Its main purpose is to facilitate hashing in hash tables, which are used by data structures like HashMap.
What is a hash key number : A hash key is the output from a hashing algorithm, where a specific input value is transformed into a distinct, unique string per input value. The purpose of hash keys in this context is to provide a surrogate key for business keys, composite business keys and business key combinations.
The integer hash function transforms an integer hash key into an integer hash result. For a hash function, the distribution should be uniform. This implies when the hash result is used to calculate hash bucket address, all buckets are equally likely to be picked. Hashing is a one-way encryption process such that a hash value cannot be reverse-engineered to get to the original plain text. Hashing is used in encryption to secure the information shared between two parties. The passwords are transformed into hash values so that even if a security breach occurs, PINs stay protected.
What are the hash values
Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.Verifying a Hash
Data can be compared to a hash value to determine its integrity. Usually, data is hashed at a certain time and the hash value is protected in some way. At a later time, the data can be hashed again and compared to the protected value. If the hash values match, the data has not been altered.The hashcode of an integer is the integer itself. Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.
What is a hashed value : A hash value is a numeric value of a fixed length that uniquely identifies data. Hash values represent large amounts of data as much smaller numeric values, so they are used with digital signatures.
Can we decrypt hash value : Hashing is a one-way process that converts a password to ciphertext using hash algorithms. A hashed password cannot be decrypted, but a hacker can try to reverse engineer it.
Why is hashing not considered encryption
Encryption is a two-way function where information is scrambled in such a way that it can be unscrambled later. Hashing is a one-way function where data is mapped to a fixed-length value. Hashing is primarily used for authentication. In a cryptocurrency blockchain, a hash is a deterministic hexadecimal number. This means that no matter how many characters the input has, the hash will always be the same number of characters. For instance, Bitcoin's hashes are always 64 digits.The most commonly used method for hashing integers is called modular hashing: we choose the array size M to be prime, and, for any positive integer key k, compute the remainder when dividing k by M. This function is very easy to compute (k % M, in Java), and is effective in dispersing the keys evenly between 0 and M-1.
What is the hash of an integer : The integer hash function transforms an integer hash key into an integer hash result. For a hash function, the distribution should be uniform. This implies when the hash result is used to calculate hash bucket address, all buckets are equally likely to be picked.
Antwort Are hash values integers? Weitere Antworten – How to hash values in C#
To create a hash for a string value, follow these steps:
A hash code is a numeric value which is used to insert and identify an object in a hash-based collection. The GetHashCode method provides this hash code for algorithms that need quick checks of object equality.A hash value is a numeric value of a fixed length that uniquely identifies data. Hash values represent large amounts of data as much smaller numeric values, so they are used with digital signatures. You can sign a hash value more efficiently than signing the larger value.
How to verify hash values : You can use Windows Powershell to calculate the SHA-256 checksum for a file.
What is hash code number
A hash code is an integer value that is associated with each object in Java. Its main purpose is to facilitate hashing in hash tables, which are used by data structures like HashMap.
What is a hash key number : A hash key is the output from a hashing algorithm, where a specific input value is transformed into a distinct, unique string per input value. The purpose of hash keys in this context is to provide a surrogate key for business keys, composite business keys and business key combinations.
The integer hash function transforms an integer hash key into an integer hash result. For a hash function, the distribution should be uniform. This implies when the hash result is used to calculate hash bucket address, all buckets are equally likely to be picked.
Hashing is a one-way encryption process such that a hash value cannot be reverse-engineered to get to the original plain text. Hashing is used in encryption to secure the information shared between two parties. The passwords are transformed into hash values so that even if a security breach occurs, PINs stay protected.
What are the hash values
Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.Verifying a Hash
Data can be compared to a hash value to determine its integrity. Usually, data is hashed at a certain time and the hash value is protected in some way. At a later time, the data can be hashed again and compared to the protected value. If the hash values match, the data has not been altered.The hashcode of an integer is the integer itself.
Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.
What is a hashed value : A hash value is a numeric value of a fixed length that uniquely identifies data. Hash values represent large amounts of data as much smaller numeric values, so they are used with digital signatures.
Can we decrypt hash value : Hashing is a one-way process that converts a password to ciphertext using hash algorithms. A hashed password cannot be decrypted, but a hacker can try to reverse engineer it.
Why is hashing not considered encryption
Encryption is a two-way function where information is scrambled in such a way that it can be unscrambled later. Hashing is a one-way function where data is mapped to a fixed-length value. Hashing is primarily used for authentication.

In a cryptocurrency blockchain, a hash is a deterministic hexadecimal number. This means that no matter how many characters the input has, the hash will always be the same number of characters. For instance, Bitcoin's hashes are always 64 digits.The most commonly used method for hashing integers is called modular hashing: we choose the array size M to be prime, and, for any positive integer key k, compute the remainder when dividing k by M. This function is very easy to compute (k % M, in Java), and is effective in dispersing the keys evenly between 0 and M-1.
What is the hash of an integer : The integer hash function transforms an integer hash key into an integer hash result. For a hash function, the distribution should be uniform. This implies when the hash result is used to calculate hash bucket address, all buckets are equally likely to be picked.