To verify that a file has not been corrupted or tampered with. By comparing the hash of a downloaded file with the original hash, a user can be sure that the file is exactly as it should be.Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.A hash value is a unique value that corresponds to the content of the file. Rather than identifying the contents of a file by its file name, extension, or other designation, a hash assigns a unique value to the contents of a file.
When should files be hashed : Hashing is also used to verify the integrity of a file after it has been transferred from one place to another, typically in a file backup program like SyncBack. To ensure the transferred file is not corrupted, a user can compare the hash value of both files.
Why do we need to hash data
Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
Why do we verify the hash value of a file : Hash values are also useful for verifying the integrity of data sent through insecure channels. The hash value of received data can be compared to the hash value of data as it was sent to determine whether the data was altered.
The hash symbol represents a command for the preprocessor, and is known as a macro. It literally tells your computer to take the code in the included file and place it where the #include statement is.
So, here, hashing is used to index and retrieve information from a database because it helps accelerate the process; it is much easier to find an item using its shorter hashed key than its original value.
How is the hash value of files useful in network
A hash function is a mathematical algorithm that converts input data into a fixed-size string of characters, known as a hash. It's a one-way process, making it difficult to reverse. Hash functions are crucial for password security, digital signatures, and data integrity verification in network communication.Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.Medium- and short-chain-3-hydroxyacyl-coenzyme A (CoA) dehydrogenase (SCHAD) (gene name, hadh) catalyze the third reaction of the mitochondrial β-oxidation cascade, the oxidation of 3-hydroxyacyl-CoA to 3-ketoacyl-CoA, for medium- and short-chain fatty acids.
Hashing verifies the file's integrity once it is transferred from one place to another in a file backup program. Users can compare the hash value of both files to ensure that transferred files are not corrupted.
What is the function of hashing : A hash function is a mathematical function that converts any digital data into an output string with a fixed number of characters. Hashing is the one-way act of converting the data (called a message) into the output (called the hash).
Does every file have a hash value : In practice, yes. A hash code (MD5, SHA-1, SHA-256) is of a fixed length, so it cannot be unique for all possible inputs. But all such hash functions are carefully designed to minimize the likelihood of a collision (two distinct files with the same hash value).
What is the point of hashes
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
Characteristics of a Good Hash Function. There are four main characteristics of a good hash function: 1) The hash value is fully determined by the data being hashed. 2) The hash function uses all the input data. 3) The hash function "uniformly" distributes the data across the entire set of possible hash values.The second version of SHA, called SHA-2, has many variants. Probably the one most commonly used is SHA-256, which the National Institute of Standards and Technology (NIST) recommends using instead of MD5 or SHA-1. The SHA-256 algorithm returns hash value of 256-bits, or 64 hexadecimal digits.
What is a useful hash function : Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.
Antwort Why do we use hash values on files? Weitere Antworten – What is the purpose of file hashing
To verify that a file has not been corrupted or tampered with. By comparing the hash of a downloaded file with the original hash, a user can be sure that the file is exactly as it should be.Hash values can be thought of as fingerprints for files. The contents of a file are processed through a cryptographic algorithm, and a unique numerical value – the hash value – is produced that identifies the contents of the file.A hash value is a unique value that corresponds to the content of the file. Rather than identifying the contents of a file by its file name, extension, or other designation, a hash assigns a unique value to the contents of a file.
When should files be hashed : Hashing is also used to verify the integrity of a file after it has been transferred from one place to another, typically in a file backup program like SyncBack. To ensure the transferred file is not corrupted, a user can compare the hash value of both files.
Why do we need to hash data
Why is hashing important Hashing is important because it offers a method for retrieving data that's secure and efficient. It's also quicker than most traditional sorting algorithms, which makes it more efficient for retrieving data.
Why do we verify the hash value of a file : Hash values are also useful for verifying the integrity of data sent through insecure channels. The hash value of received data can be compared to the hash value of data as it was sent to determine whether the data was altered.
The hash symbol represents a command for the preprocessor, and is known as a macro. It literally tells your computer to take the code in the included file and place it where the #include statement is.

So, here, hashing is used to index and retrieve information from a database because it helps accelerate the process; it is much easier to find an item using its shorter hashed key than its original value.
How is the hash value of files useful in network
A hash function is a mathematical algorithm that converts input data into a fixed-size string of characters, known as a hash. It's a one-way process, making it difficult to reverse. Hash functions are crucial for password security, digital signatures, and data integrity verification in network communication.Hashing is a one-way mathematical function that turns data into a string of nondescript text that cannot be reversed or decoded. In the context of cybersecurity, hashing is a way to keep sensitive information and data — including passwords, messages, and documents — secure.Medium- and short-chain-3-hydroxyacyl-coenzyme A (CoA) dehydrogenase (SCHAD) (gene name, hadh) catalyze the third reaction of the mitochondrial β-oxidation cascade, the oxidation of 3-hydroxyacyl-CoA to 3-ketoacyl-CoA, for medium- and short-chain fatty acids.

Hashing verifies the file's integrity once it is transferred from one place to another in a file backup program. Users can compare the hash value of both files to ensure that transferred files are not corrupted.
What is the function of hashing : A hash function is a mathematical function that converts any digital data into an output string with a fixed number of characters. Hashing is the one-way act of converting the data (called a message) into the output (called the hash).
Does every file have a hash value : In practice, yes. A hash code (MD5, SHA-1, SHA-256) is of a fixed length, so it cannot be unique for all possible inputs. But all such hash functions are carefully designed to minimize the likelihood of a collision (two distinct files with the same hash value).
What is the point of hashes
The main purpose of hashing is to verify the integrity of a piece of data. Since the hash generated is UNIQUE to the input data, it acts as a unique “fingerprint” of the input data. This makes a hash useful for verifying the integrity of data sent through insecure communication channels like the internet.
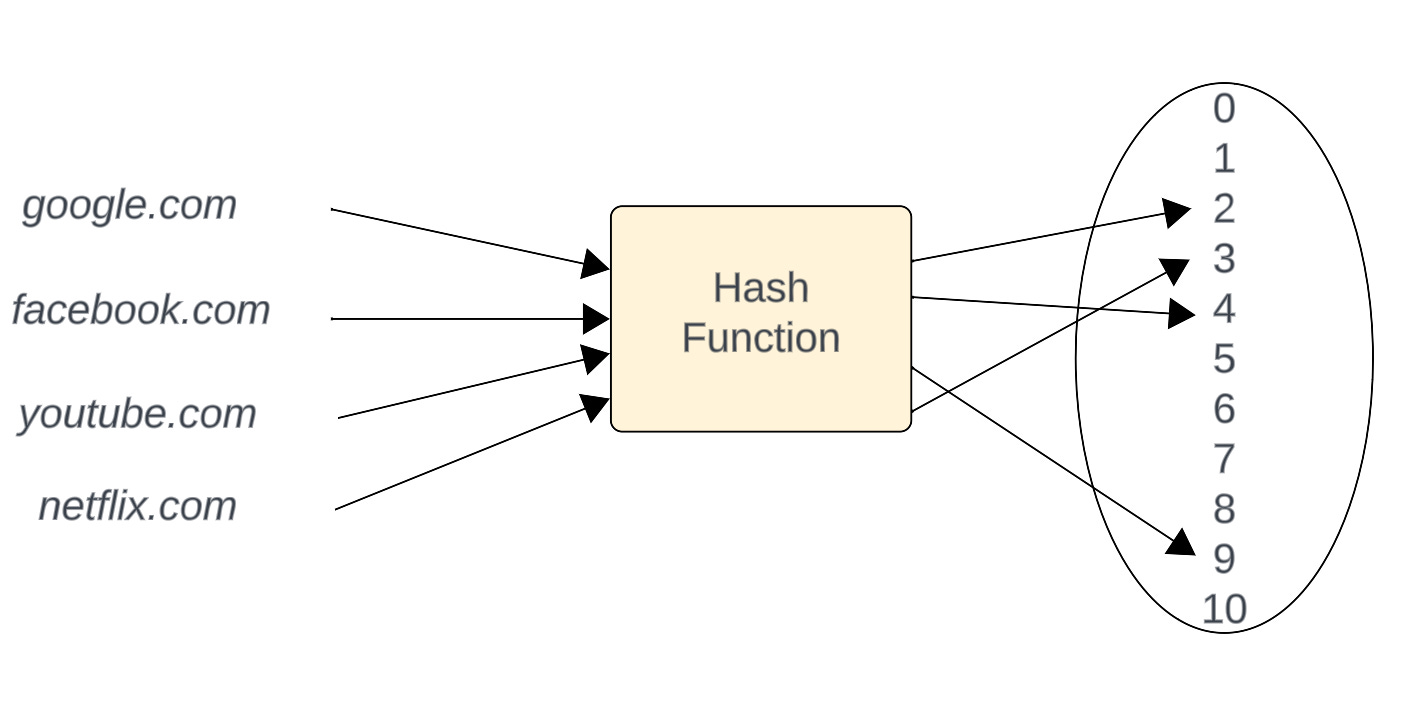
Characteristics of a Good Hash Function. There are four main characteristics of a good hash function: 1) The hash value is fully determined by the data being hashed. 2) The hash function uses all the input data. 3) The hash function "uniformly" distributes the data across the entire set of possible hash values.The second version of SHA, called SHA-2, has many variants. Probably the one most commonly used is SHA-256, which the National Institute of Standards and Technology (NIST) recommends using instead of MD5 or SHA-1. The SHA-256 algorithm returns hash value of 256-bits, or 64 hexadecimal digits.
What is a useful hash function : Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves.