SHA-256 is a cryptographic (one-way) hash function, so there is no direct way to decode it. The entire purpose of a cryptographic hash function is that you can't undo it.To convert Sha256 to string, you can use a built-in function in most programming languages called hexdigest(). This function takes the Sha256 value and converts it into a string of hexadecimal characters. This string can then be used or displayed as needed.No, we can't decrypt a hash of any message to get the original message, because hash function is. One-way function means that we can execute this function easily for any input for finding answer. But it is impossible to find that input from received output with using any function.
How to decrypt SHA256 in Linux : SHA256 is a one-way hashing algorithm. There is no direct method for SHA256 decryption. SHA256 is decrypted by using Trial & Error methodology. It may take some time if either the text that will be decrypted or the character set that will be used for decryption is long.
Why is SHA-256 unbreakable
Because SHA-256 is a one-way cryptographic algorithm, it's impossible to reverse-engineer the input from the output hash. This means that miners can't cheat the system by submitting a fake solution since other nodes on the network can easily verify the answer by checking the hash.
How long does SHA-256 take to crack : SHA-256 GPU machine cracking 8 characters with combination of lowercase (l), uppercase (u), special character(s), digits (d) in 2nd to 7th character while making the 1st character fixed for special characters(s) and 8th character fixed for uppercase (u) brings the cracking time to only 6 mins while just making the 1st …
SHA-256 GPU machine cracking 8 characters with combination of lowercase (l), uppercase (u), special character(s), digits (d) in 2nd to 7th character while making the 1st character fixed for special characters(s) and 8th character fixed for uppercase (u) brings the cracking time to only 6 mins while just making the 1st …
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Is it possible to decrypt hash
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.Hashing is one-way and irreversible, meaning it is computationally infeasible to retrieve the original data from the hash value.SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted. What you probably want is reversing hashed value to normal text. that's the idea behind hashing – so that if somebody has your data they cannot “read it”.
It's also really hard to break. For example, hashing algorithms should be irreversible, but aren't always. SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value.
How fast can SHA-256 be cracked : SHA-256 cracking performance with CPU machine. Using uppercase only character (u) it takes 15sec for 6-character long password HELLO to crack where 8-character long password “MYSECRET” takes 20 mins and it finishes checking all the combination of 8 characters roughly in 38 mins.
Can you brute-force SHA-256 : Yes, SHA-256 can be brute forced using specialized tools and algorithms. However, due to the complexity of the algorithm, it would take an immense amount of computing power to execute a successful attack, making it unlikely to be successful in most situations.
Can a quantum computer break SHA-256
Quantum computers also threaten the security of hash functions like SHA-256 by utilizing Grover's algorithm. Grover's algorithm can search unsorted databases quadratically faster than classical algorithms, making brute-force attacks on hash functions more feasible.
AES-256 encryption is virtually uncrackable using any brute-force method. It would take millions of years to break it using the current computing technology and capabilities.SHA-256 ensures data remains unchanged during transmission. Once data is hashed, it cannot be reversed or decrypted to retrieve the original data.
Can encrypted hashes be cracked easily : Dictionary lists and other tools make this task a bit easier for an attacker in a hybrid attack, but the time needed to crack a hashed password can get astronomical quickly. Different hashing algorithms take different amounts of time for password cracking software and hardware to crack.
Antwort Can SHA-256 decrypt? Weitere Antworten – Is it possible to decrypt SHA-256
SHA-256 is a cryptographic (one-way) hash function, so there is no direct way to decode it. The entire purpose of a cryptographic hash function is that you can't undo it.To convert Sha256 to string, you can use a built-in function in most programming languages called hexdigest(). This function takes the Sha256 value and converts it into a string of hexadecimal characters. This string can then be used or displayed as needed.No, we can't decrypt a hash of any message to get the original message, because hash function is. One-way function means that we can execute this function easily for any input for finding answer. But it is impossible to find that input from received output with using any function.
How to decrypt SHA256 in Linux : SHA256 is a one-way hashing algorithm. There is no direct method for SHA256 decryption. SHA256 is decrypted by using Trial & Error methodology. It may take some time if either the text that will be decrypted or the character set that will be used for decryption is long.
Why is SHA-256 unbreakable
Because SHA-256 is a one-way cryptographic algorithm, it's impossible to reverse-engineer the input from the output hash. This means that miners can't cheat the system by submitting a fake solution since other nodes on the network can easily verify the answer by checking the hash.
How long does SHA-256 take to crack : SHA-256 GPU machine cracking 8 characters with combination of lowercase (l), uppercase (u), special character(s), digits (d) in 2nd to 7th character while making the 1st character fixed for special characters(s) and 8th character fixed for uppercase (u) brings the cracking time to only 6 mins while just making the 1st …
SHA-256 GPU machine cracking 8 characters with combination of lowercase (l), uppercase (u), special character(s), digits (d) in 2nd to 7th character while making the 1st character fixed for special characters(s) and 8th character fixed for uppercase (u) brings the cracking time to only 6 mins while just making the 1st …
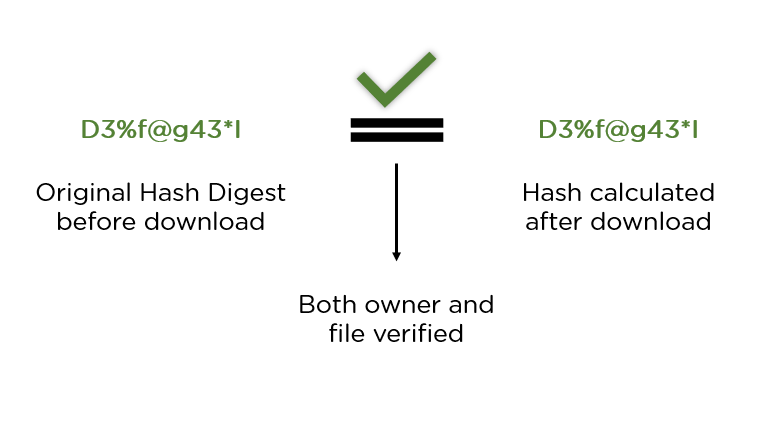
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Is it possible to decrypt hash
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.Hashing is one-way and irreversible, meaning it is computationally infeasible to retrieve the original data from the hash value.SHA256 is a hashing function not an encryption function. Since SHA256 is not an encryption function, it cannot be decrypted. What you probably want is reversing hashed value to normal text. that's the idea behind hashing – so that if somebody has your data they cannot “read it”.

It's also really hard to break. For example, hashing algorithms should be irreversible, but aren't always. SHA-256 is strong enough to prevent hackers from deriving the original message from the hash value.
How fast can SHA-256 be cracked : SHA-256 cracking performance with CPU machine. Using uppercase only character (u) it takes 15sec for 6-character long password HELLO to crack where 8-character long password “MYSECRET” takes 20 mins and it finishes checking all the combination of 8 characters roughly in 38 mins.
Can you brute-force SHA-256 : Yes, SHA-256 can be brute forced using specialized tools and algorithms. However, due to the complexity of the algorithm, it would take an immense amount of computing power to execute a successful attack, making it unlikely to be successful in most situations.
Can a quantum computer break SHA-256
Quantum computers also threaten the security of hash functions like SHA-256 by utilizing Grover's algorithm. Grover's algorithm can search unsorted databases quadratically faster than classical algorithms, making brute-force attacks on hash functions more feasible.
AES-256 encryption is virtually uncrackable using any brute-force method. It would take millions of years to break it using the current computing technology and capabilities.SHA-256 ensures data remains unchanged during transmission. Once data is hashed, it cannot be reversed or decrypted to retrieve the original data.
Can encrypted hashes be cracked easily : Dictionary lists and other tools make this task a bit easier for an attacker in a hybrid attack, but the time needed to crack a hashed password can get astronomical quickly. Different hashing algorithms take different amounts of time for password cracking software and hardware to crack.